Microsoft has recently announced the Object Replication for Premium Block Blob Storage. This feature is in public review. Let look at why we need this and what are the benefits of having them, Specially how to setup this one

Object replication asynchronously copies block blobs in a container according to rules that you configure. The contents of the blob, any versions associated with the blob, and the blob's metadata and properties are all copied from the source container to the destination container
few things to note
- Object replication does not support blob snapshots
- Object replication is supported when the source and destination accounts are in the hot or cool tier.
Before you proceed you need to know following
- Replication Policies - Replication policy is an object that holds replication rules in the target region. You need to create the replication policies on the destination side and associate them with the source.
• Source can replicate to multiple destination (in the same target account) using a single policy
• Source account can replicate to maximum of two accounts - Replication Rules - Replication Policies - Replication policy is an object that holds replication rules in the target region. You need to create the replication policies on the destination side and associate them with the source.
• Each replication rule defines a single source and destination container
• You can specify up to 10 replication rules for each replication policy
How to Guide
Following is my source and destination

Browse to the source storage account and create the policy
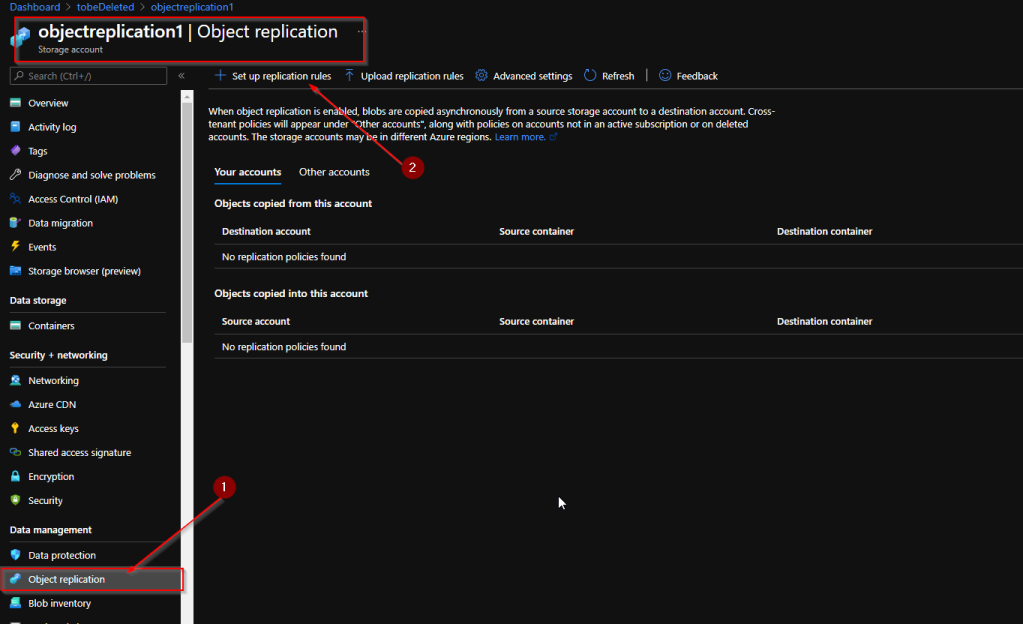
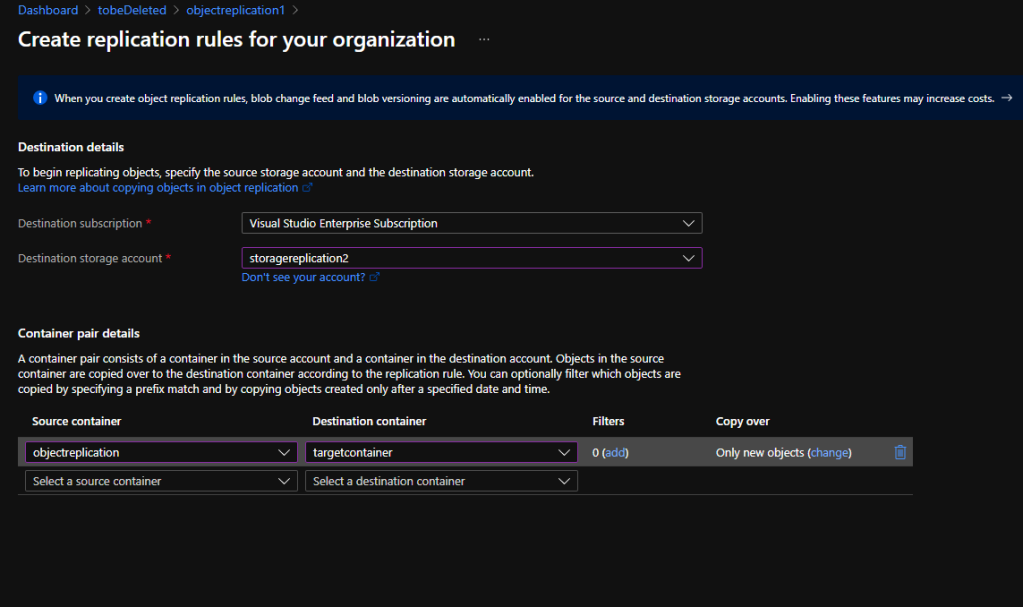
Once you select the above you will get into the below page which where you need to define the source and destination containers
Note : A container pair consists of a container in the source account and a container in the destination account. Objects in the source container are copied over to the destination container according to the replication rule. You can optionally filter which objects are copied by specifying a prefix match and by copying objects created only after a specified date and time
During the process you can specify the copy over status which mean what will be getting copied to the target. if you select custom you can specify a date range
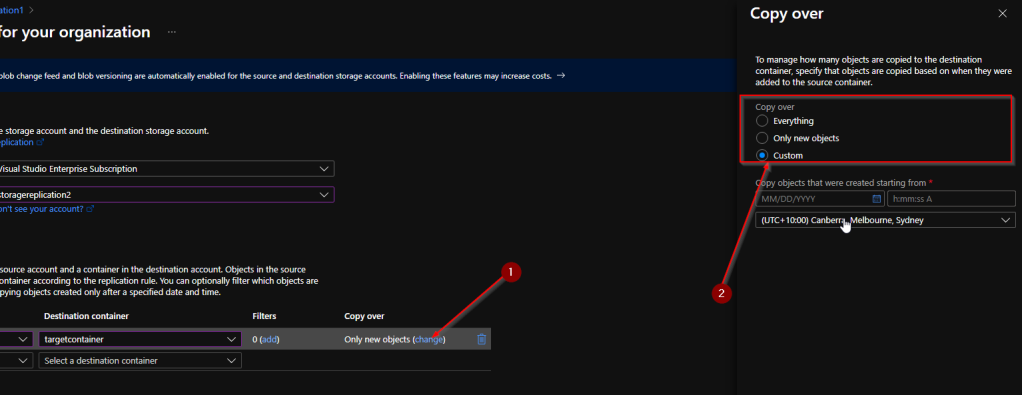
Once you done hit save and apply

Once done you can see the changes in both source and destination storage accounts
Because block blob data is replicated asynchronously, the source account and destination account are not immediately in sync. There's currently no SLA on how long it takes to replicate data to the destination account.
For more details head out to the MS documentation which will have up to date features
https://docs.microsoft.com/en-us/azure/storage/blobs/object-replication-overview?tabs=powershell
Comments
Post a Comment