Recently I delivered a session on Azure Virtual Desktop App Attach. It's quite fascinating. If we look at the solution carefully we will realize with the MSIX app attached AVD will become almost a management-less solution. in this we are separating the apps from the base operating system.
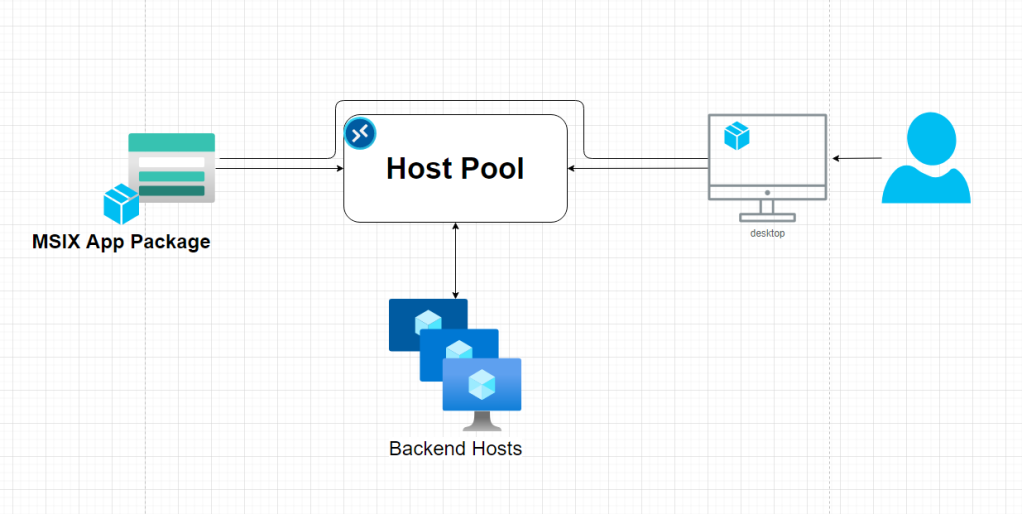
With MSIX app attach,
- You don’t need to maintain gold images
- You can attach the same package to multiple hosts
- Could save more on storage and maintaining storage and updates
- Etc
So, before we get into how to do this
You need to know what MSIX, and App attach is means
- MSIX – MSIX is the next generation format of application packages, previously we have MSI and now MSIX, what’s different with MSIX is, the application is running in a containers
- App attach - App attach is the method of delivery for MSIX packages to the AVD
Pre-requests
- App packaging environment
- MSIX packaging tool
- Working Azure Virtual desktop solution integrated with Active Directory Domain Services.
- Storage Accounts to host the packages in the cloud
- A Certificate (Prefer if you can have a publicly signed certificate)
Preparing the packaging environment
If you are using Hyper-V, you can use hyper v quick create to use Microsoft’s pre-setup template for app packaging


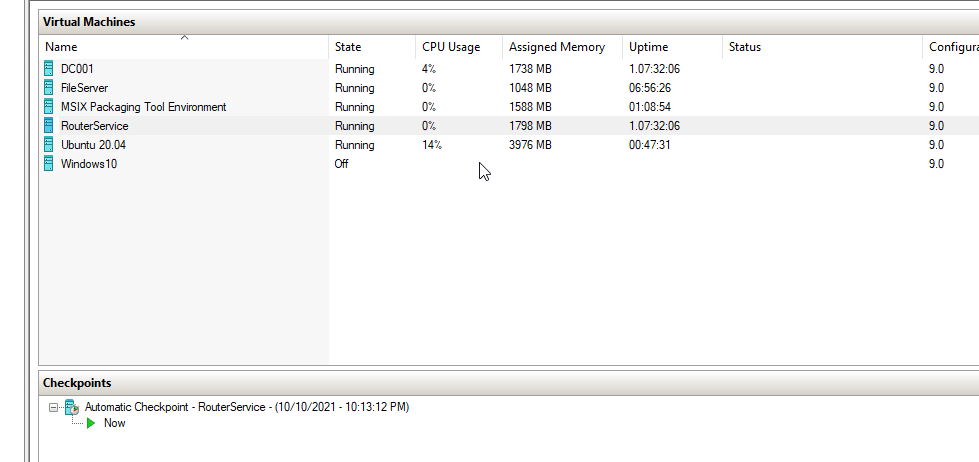
If you use that option, you will get VM as shown above, this VM will only have the required tools and the basic. Specially the “MSIX Packaging Tool”
Let begin. :D
Login to the App packaging VM and open “MSIX Packaging Tool” and select Create

And follow the instructions as below


Now select the installer.

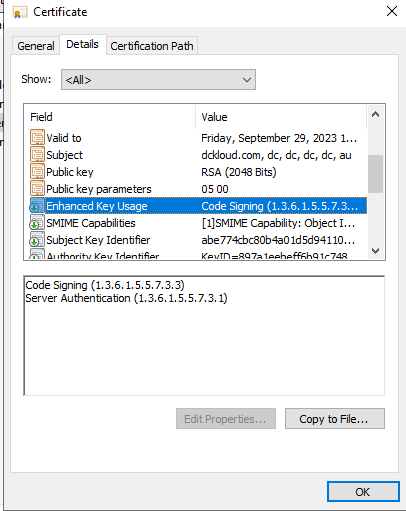
And down the bottom selects your PFX file to sign the package. This is mandatory to sign the package and what you need to keep in mind is your cert needs to be code signing enabled as below if not package signing will failed
Fill in the package details as you need

Once you hit next, wizard will automatically launch the installer, what will happen at the same time tool will create a snapshot of the system and start capturing all the changes after that point until we confirm the application installation is completed. Just install the application as normal hear I’m installing visual studio code

Once the setup is completed, the tool will automatically identify its been completed and prompt you with below
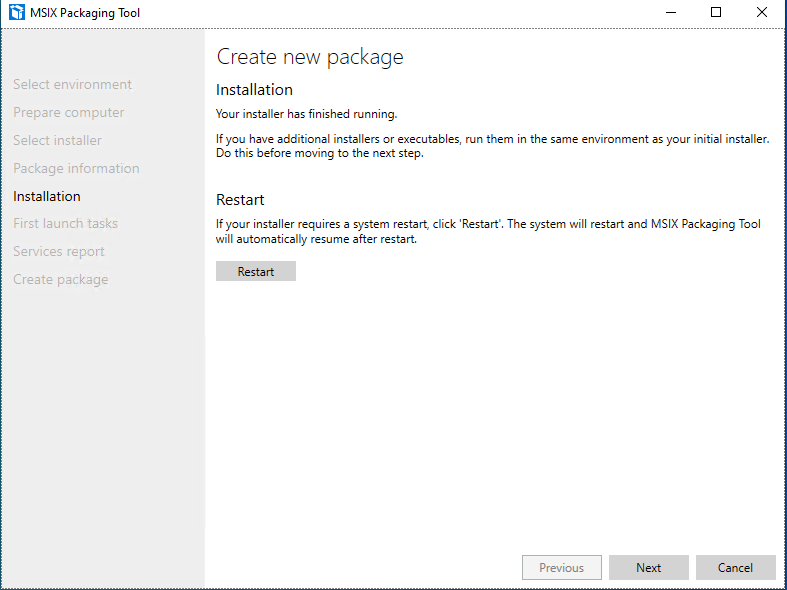
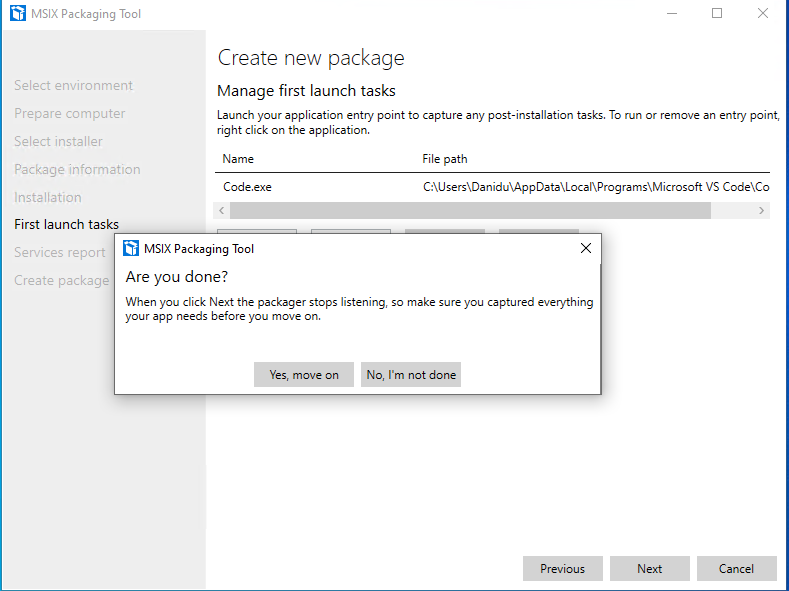
If you are done with packaging hit next, and as I mentioned packing tool will look for all the changes within the window

Select “Yes Move on” and it will prepare our MSIX Package.
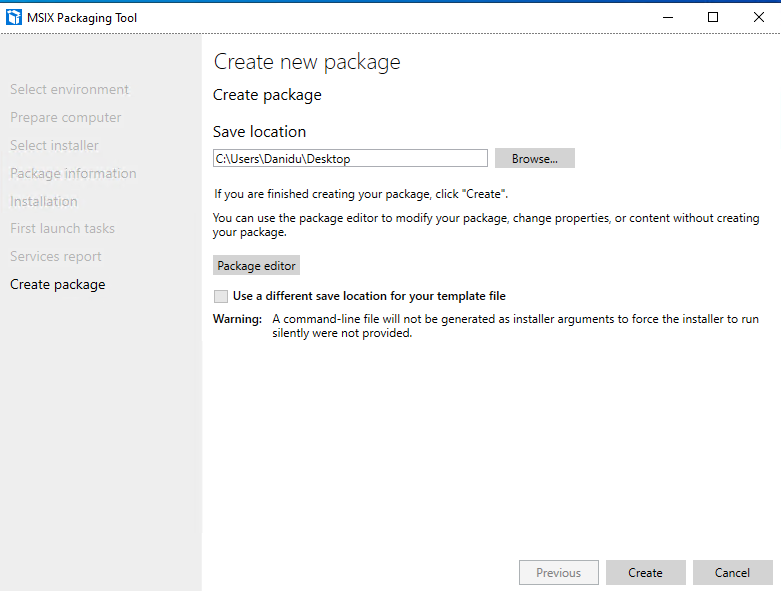
I have skipped few screenshots, just to keep things short once done you need to select the destination
If the packaging is successful, it will provide the below notification confirming the packing

In the next articles. let’s deep dive into how to convert this MSIX and use it in our AVD Environment.
Continued…
Comments
Post a Comment