Organizations commonly use private IP addresses for internal communication in their private networks. When these networks are connected using VPN over the Internet or across private WAN, the address spaces must not overlap otherwise the communication would fail.
To connect two or more networks with overlapping IP addresses, NAT is deployed on the gateway devices connecting the networks. Previously customers needed to use Cisco strech network appliances to connect Azure and their on prem data centre.
I was part of a similar migration we were using CISCO CSR 1000V virtual appliance to strech the onprem network to Azure. and we had to face lot of challenges with routing, packet sizes etc...
There are many reasons that we need to use same IP addresses in both onprem and Azure specially when in a hybrid cloud or a migration scenario. Now with this feature hopefully things will be seamleess
Below is the example from Microsoft Documentation.
NAT example
The following diagram shows an example of Azure VPN NAT configurations:
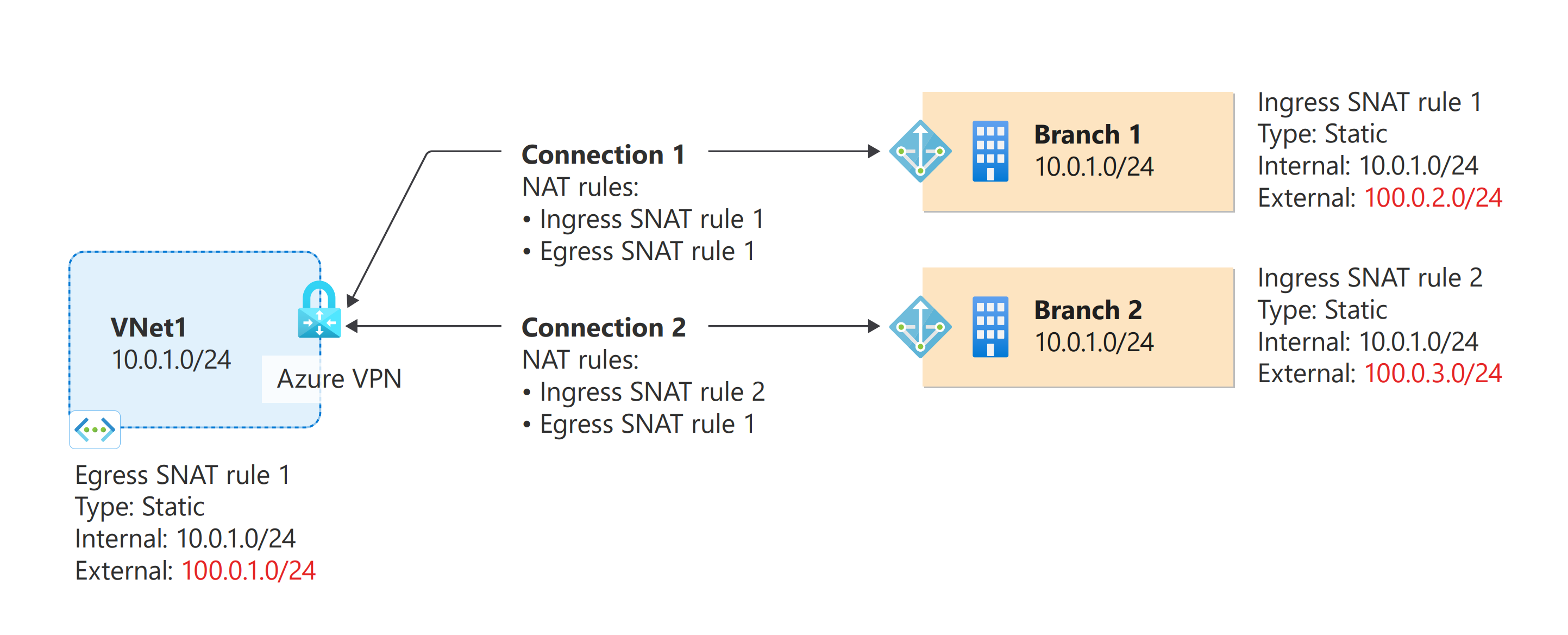
The diagram shows an Azure VNet and two on-premises networks, all with address space of 10.0.1.0/24. To connect these two networks to the Azure VNet and VPN gateway, create the following rules:
- IngressSNAT rule 1: This rule translates the on-premises address space 10.0.1.0/24 to 100.0.2.0/24.
- IngressSNAT rule 2: This rule translates the on-premises address space 10.0.1.0/24 to 100.0.3.0/24.
- EgressSNAT rule 1: This rule translates the VNet address space 10.0.1.0/24 to 100.0.1.0/24.
In the diagram, each connection resource has the following rules:
- Connection 1 (VNet-Branch1):
- IngressSNAT rule 1
- EgressSNAT rule 1
- Connection 2 (VNet-Branch2)
- IngressSNAT rule 2
- EgressSNAT rule 1
Based on the rules associated with the connections, here are the address spaces for each network:
| Network | Original | Translated |
|---|---|---|
| VNet | 10.0.1.0/24 | 100.0.1.0/24 |
| Branch 1 | 10.0.1.0/24 | 100.0.2.0/24 |
| Branch 2 | 10.0.1.0/24 | 100.0.3.0/24 |
The diagram below shows an IP packet from Branch 1 to VNet, before and after the NAT translation:
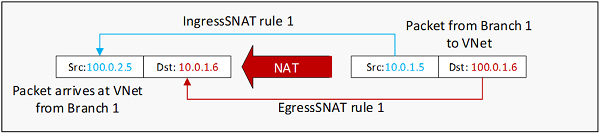
https://docs.microsoft.com/en-us/azure/vpn-gateway/nat-overview#example
In near future I will be doing a youtube video on this feature.
Comments
Post a Comment